Author: John Farley

Social engineering is an attack vector where criminals exploit our natural tendencies to trust other people. There are many ways to execute a social engineering attack. Some of the most common social engineering crimes come in the form of phishing emails and malicious phone calls. All of these methods involve impersonations where unsuspecting victims are often manipulated into transferring large sums of money or other sensitive data to criminals.
Social engineering attacks continue to plague businesses both large and small across virtually all industry sectors. Criminals have continued their assault with the goal of executing funds transfer schemes and ex-filtrating sensitive data that can be monetized.
Their business models have been a smashing success, as evidenced by the2022 Internet Crime Report, which the Federal Bureau of Investigation's Internet Crime Complaint Center (IC3) issued in March, 2023.* The crime report highlights a staggering $10.3 billion in internet crime losses in 2022, increasing every year over the past 5 years.
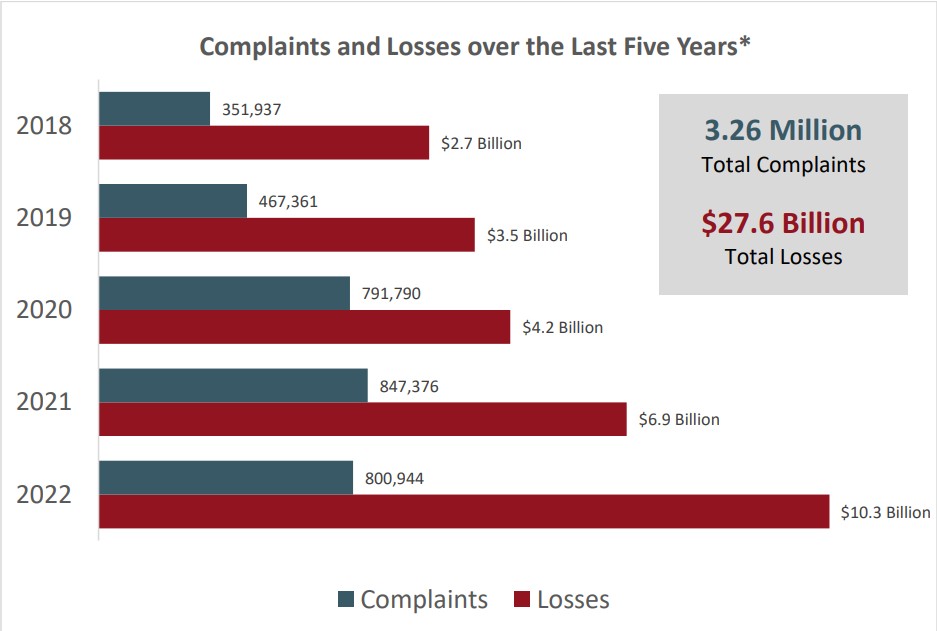
The 2022 losses were driven by business email compromise (BEC) schemes with losses over $2.7 billion. In a BEC scam, criminals get access to a business email account and other forms of communication such as phone numbers and virtual meeting applications. They then access that email account to defraud the company, its employees, vendors and trading partners by making unauthorized funds transfers.
Preventing social engineering attacks
Any organization can implement several strategies to help prevent social engineering attacks and BEC scams:
- Implement training programs to help employees to identify a phishing email and educate employees not to open suspicious emails. Be wary of unexplained urgency, last-minute changes to instructions and refusal to confirm via telephone or video call.
- Implement safeguards when sending wires, such as requiring phone calls to confirm details of a transaction. Limit who can handle requests for sensitive information, such as W-2s, and approve or process wire transfers.
- Regularly monitor and test business email accounts to ensure rules haven't been created that reroute emails to unauthorized or unintended destinations.
- Don't respond to an email requesting funds or sensitive information. Instead, contact the purported executive using some other channel of communication, such as a phone call directly to the executive.
- Keep lists of key internal contacts and external vendors with information for anyone authorized to request or approve changes in payment instructions and require multiple approvals for certain wire transfers, such as those involving amounts more than a designated threshold. It's preferable for the lists to be on paper and not in electronic files.
- Inform banks and regular trading partners that they must confirm any changes in payment instructions in a pre-determined way, such as calling a specified contact person to validate the change request.
Mitigating a social engineering financial loss
If your company has been attacked successfully, and a financial transfer was completed, there are a few ways to mitigate risk and exposure.
- Immediately notify the remitting and receiving banks and seek to freeze funds if possible. If the transfer is caught within 48 hours, the bank may be able to recover some or all of the funds. Also, engage experienced legal counsel as soon as possible to maximize the chance of freezing the funds.
- Compile copies of the emails documenting the fraud with details of the fraudster's account receiving the funds.
- Report the incident to local law enforcement agencies as soon as possible, particularly in the receiving jurisdiction. These authorities often have the power to freeze funds, helping the victim avoid costs for obtaining court orders on their own. These crimes can be reported to the joint FBI/National White Collar Crime Center — Internet Crime Complaint Center (IC3) website at ic3.gov.
- Initiate civil action against the criminal. It's likely the recipient of the funds won't answer the civil action, enabling the victim to enter a default judgment on its full claim by default. However, recovering the funds could be difficult.
- Hire an independent forensic investigator to identify the extent of the network intrusion. These investigators can tell what information may have been accessed and give advice on actions to take to add security features as appropriate.
- Determine through legal counsel whether you have any reporting obligations to regulators, business partners or other affected individuals.
Additional resources: Gallagher's Cyber Risk Management team
Gallagher's Cyber Risk Management team is available to help our clients of all sizes combat the threat of cybercrime and social engineering. From phishing training and simulations to pre-recorded employee training through Cyber Defense Center or more customized training solutions, Gallagher can help shore up the key first line of defense for cybercrime — your employees.
Our phishing campaigns are built from scratch and fully customized to our clients' needs, enabling our clients to sharpen awareness in preventing cyber attacks and cybercrime losses.
Contact us to learn more or to book a 30-minute consultation today.


